Managing (and hosting) your own WordPress website gives you a lot of freedom in how you configure and manage your site, but unfortunately, this freedom also comes with extra responsibility. You need to ensure your site is well-protected. This means safeguarding your WordPress site against hackers, spam comments, and brute force attacks.
Why is your website being attacked?
Maybe you’ve seen inside the website log files that bots or hackers are searching for non-existent theme or plugin files. This way, hackers try to find insecure plugins and themes to break into your website. How do hackers know this? Because WordPress is open-source, the code of unsafe themes and plugins is also public.
Another common target for hackers is the login page. Often, an insecure password is used, making it easy for hackers to take over a website. So, they might try it on your website too.
We regularly deal with hacking attempts on our own and our clients’ websites. Despite regular updates and monitoring of insecure plugins and themes, these websites are still targeted by hackers. In this blog post, we will discuss the risks and measures you can take.
What attacks should you protect your WordPress website from?
There are various ways your website can be attacked. The most common are:
- Brute force attacks on your login page: Bots try different username and password combinations to gain access to your website.
- Comment Spam: Bots attempt to post spam comments, even on blog posts where comments are disabled.
- Searching for insecure themes and plugins: Bots search for files within your website that contain vulnerabilities.
- Indexing your site: Bots scan all your pages and use this information for other purposes. Recently, there’s been a lot of discussion about indexing websites for training AI.
- Spam via any type of subscription forms: Spambots target opt-ins and contact forms.
All these attacks generate more load on your web server than regular visitors. The issue with WordPress, or rather the PHP code that is executed for each page view, is that it uses RAM and CPU. Both resources are limited, and the more they are used by bots or hackers, the less there is available for your important visitors. While you can’t completely prevent these attacks, there are ways to mitigate them.
Securing your WordPress website in 5 steps
1) Install a Cache Plugin
The easiest way to limit the execution of PHP scripts is by using a cache plugin. A cache plugin creates a copy of each page or post and serves the cached version instead of regenerating the page each time. Using a cache module or plugin also speeds up your website!
What are the options?
We use WP Rocket or the cache module of NGINX. WP Rocket not only creates the cached version of a page but also optimizes the HTML source code, making the website load even faster. The NGINX cache works basically like a cache plugin but lacks optimization options.
Ask your hosting provider if they use the NGINX cache; if not, use WP Rocket or another cache plugin for your WordPress website.
When using Cloudflare (see below), you can also cache pages. This reduces server load and serves your files via a CDN, allowing visitors worldwide to access your site faster.
2) Block unwanted bots
There are good and bad bots. You definitely want Google or Bing bots to index your site, but many other bots shouldn’t be on your website. They usually request many pages in a short time, potentially slowing down your site for other visitors or even causing it to become unresponsive. It’s better to keep them away.
What can you do?
Use Cloudflare’s web filter (proxy). Even with the free version, you can block many bad bots. Cloudflare also has tools to speed up your website for visitors.
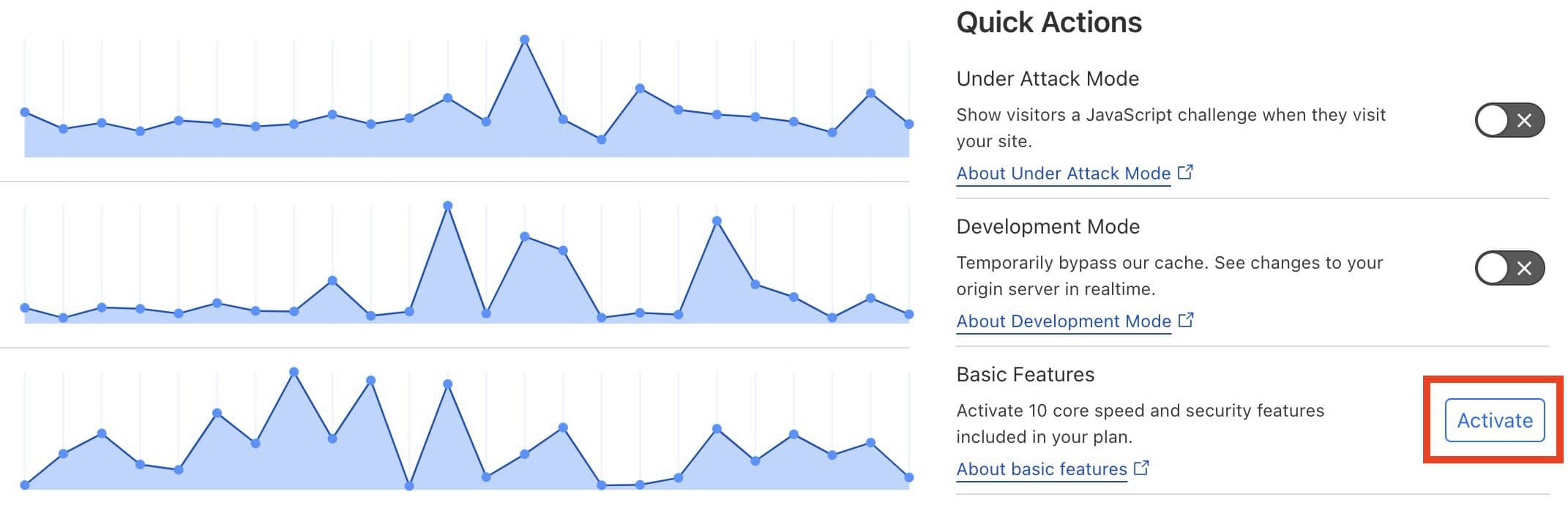
Enable Cloudflare basic settings
Besides Cloudflare, we use the WordPress Plugin NinjaFirewall for every site. It provides a Web Application Firewall (WAF) with hundreds of “Security Rules” to block hackers and bots. You can also add your own rules to block bots based on their name.
Protect your login and registration pages
The WordPress login page is particularly popular with hackers. Websites with weak passwords and no extra security are frequently hacked. If such an attack happens to your WordPress website, there’s no need to worry immediately, but you do want to prevent it. During such an attack, a bot or hacker tries as many username/password combinations as possible in a short period. This puts extra load on your website and unnecessarily uses a lot of RAM and CPU.
How can you secure the login page?
NinjaFirewall has an option to block such “Brute Force” attacks. When someone enters the wrong combination multiple times, a captcha challenge appears. Bots are also recognized and immediately blocked.
With Cloudflare, you can set up a rule that provides similar protection even before the bot or hacker will reach your website.
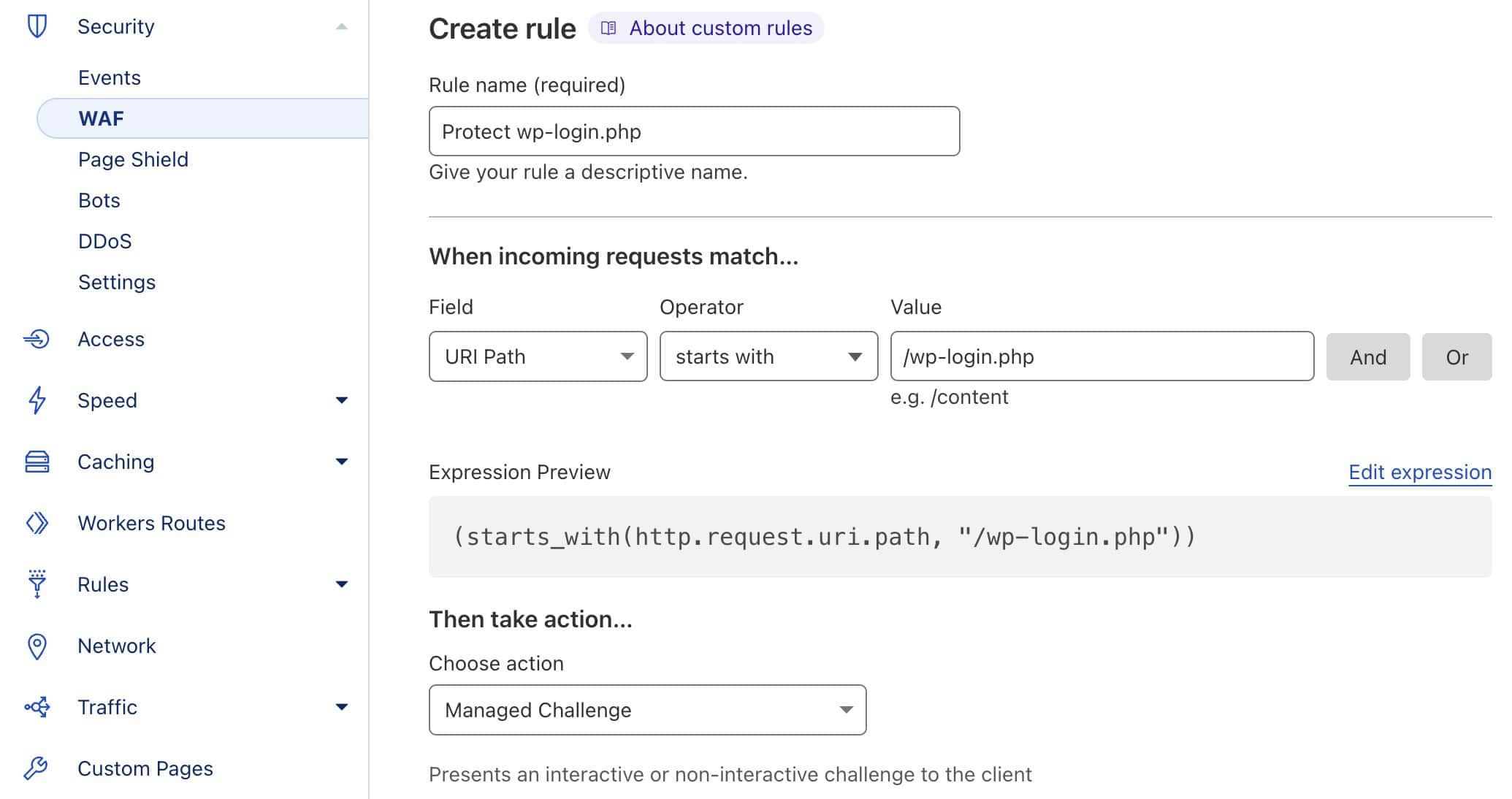
Cloudflare – Custom rule the WP Login page
For securing these “standard” WordPress forms, you can install the WP Armour plugin. This plugin uses a “honeypot” function that places fake fields inside the form. Bots are recognized and blocked after filling in these fields. We find that WP Armour is a good addition to the other options.
You can also restrict the login page to your own IP addresses, but this may prevent you from logging in when you’re on the go.
4) Use a Static 404 – Not found page
A major issue with WordPress and other PHP applications is that almost all requests are handled by a single PHP file, including those for non-existent files. This way, WordPress is responsible for handling all 404 – not found errors. With the problem that all standard database queries are executed for each 404 error, just like the homepage or a blog post.
Whenever hackers and bots search for files within your website, they produce a lot of 404 errors. If there are a lot of requests, your website can become slow or unresponsive.
Static 404 error page
How do you prevent this issue?
For non-existent static files (e.g., images, JS, and CSS files), it’s better to show a static 404 page. Here are the steps:
- Create an HTML file named 404.html.
- Fill this page with a short text and a link to the homepage. You can use the 404 page from your WordPress theme for content.
- Upload the 404 page to the public_html folder of your web hosting account.
- Use the following instruction to tell the NGINX web server to call a different 404 page for requests with the listed file extensions. Place this code in the NGINX configuration just below the block that starts with “Location /…”. There might already be a similar instruction, in which case you should replace it.
Not sure or doesn’t the modification work as expected? Ask your hosting provider to make this change for you.
If your hosting package is based on Apache, you can paste the following code into the .htaccess file of your website (just above the instructions placed by WordPress):
Protect your web forms
If your web forms aren’t adequately protected, bots will repeatedly attempt to send spam. Besides the nuisance and clutter, these submissions can cause the following issues:
- Your website sends spam to your email addresses, causing legitimate submissions to end up in the spam box.
- Your SMTP or mail provider places your email address on the suppression list, preventing you from sending and/or receiving messages.
- Spam bots use third-party addresses to sign up for your mailing list without consent. Sending newsletters to these addresses violates GDPR regulations.
How can you better protect web forms?
The WP Armour plugin protects forms from the most popular contact form plugins. For others, you can use available anti-spam functions (e.g., ReCaptcha).
Cloudflare can also help protect forms. In Cloudflare, go to Security > WAF > Custom Rules. Use a rule to protect your pages which contain a form.
Our own contact form plugin has built-in features for spam protection.
You see that you can secure your website quite well with Cloudflare, NinjaFirewall and WP Armor. Not sure about your security? Always ask your web developer or hosting provider.
More tips to keep your website secure
- Choose good WordPress plugins. Popular plugins in the WordPress repository are regularly updated and should be safe. Plugins are reviewed daily, and if a security issue is found, the plugin owner will be notified to fix it.
- Always download plugins from the WordPress repository or the plugin developer’s website. Entire packages of premium plugins offered by a third party for a very low price can contain viruses and spyware.
- Update your website regularly. This prevents unresolved security issues.
- Regularly check log files for irregularities. Look out for many 404 errors or thousands of requests from the same IP address. Block these IP addresses if possible.
- Choose a hosting provider with DDoS protection. Better hosting providers offer this protection by default at no extra cost. The chance of your website being the victim of a DDoS attack is small, but it’s an extra layer of security.
Do you know of an important security measure not mentioned in our blog post? Send us a message, we are very curious.
Published in: Tutorials